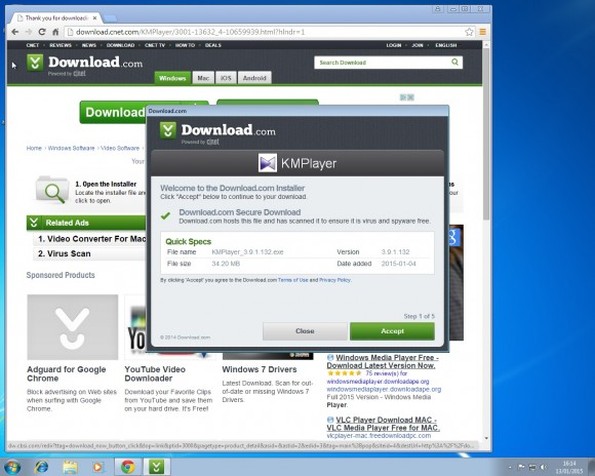
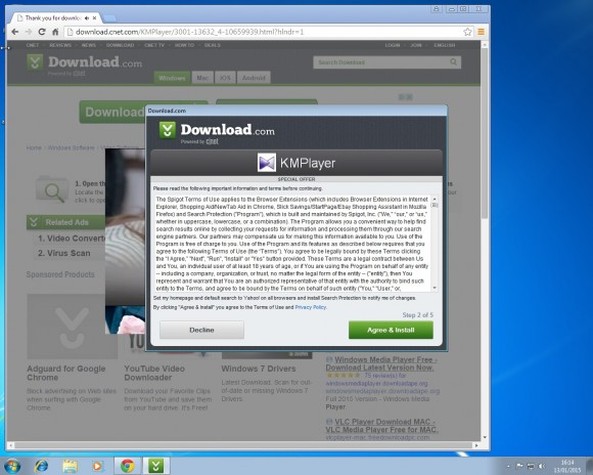
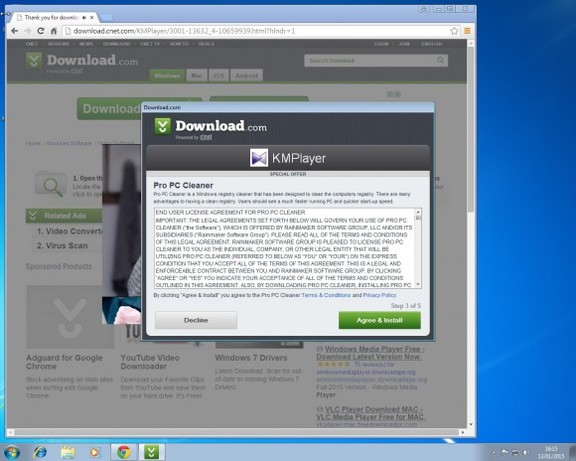
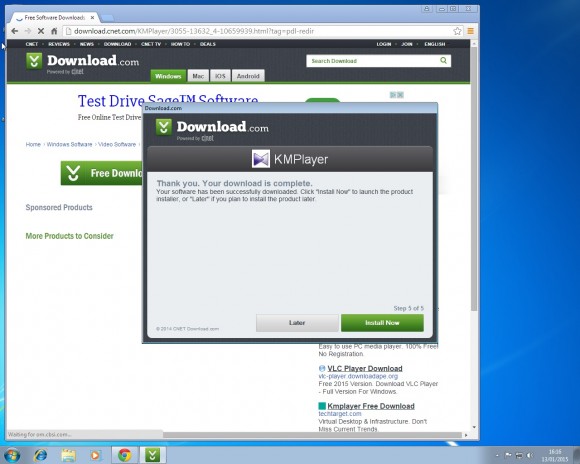
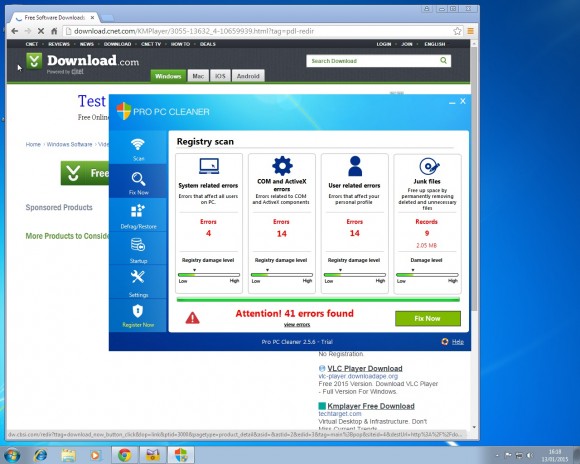
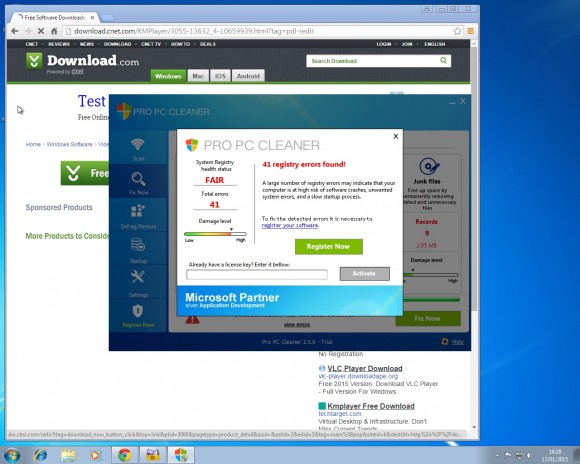
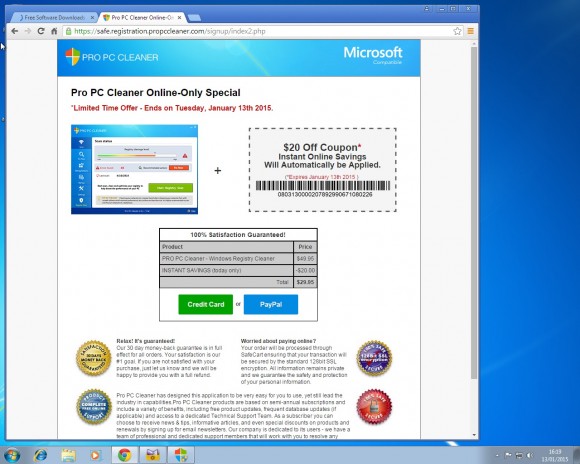
Welcome to PC Tech for Hire, Montgomery Alabama's professional residential and small business computer repair and service provider. Thanks to Cadishead Computers for the use of this series of articles. KMPlayer Following on from part 1 of our series “what happens when you install the top 20 download.com apps” – Avast. We are now onto no 2 on the list KMPlayer. What is KMPlayer? Well according to download.com it has evolved from a video player to a leading source for content discovery. EDITOR: Whatever that means! The applications record breaking viewership and the use of its flagship media is most visible in the gaming front, with a successful casting of Season 3 of the League of Legends World Championship. Alongside other forays into e-sports, like GOM and Starcraft 2….. Blah.. So, how did we do with KMPlayer? First, do you see the ‘Installer Enabled’ Under the download now button?. It’s kinda grey, and it by itself doesn’t appear to be anything obtrusive.. Or so you would think. Part 1. Ok, this is fine, however this is step 1 of 5? Step 2: You are agreeing to the following: The Spigot Terms of Service (which you have agreed to, because you have clicked Agree and Install) Browser Extensions in Internet Explorer. Shopping Aid / New Tab Aid in Google Chrome Slick Savings / Start Page / Ebay Shopping Assistant in Mozilla Firefox. Finally Search Protection! All the above just by clicking agree and install. So irrespective of which internet browser you use, it WILL be affected in some shape or form. Note how the Decline button is greyed out. Making it appear that you can not click on it? So we click Agree and Install on Step 3 of 5. This time, we have agreed to Pro PC Cleaner. Which is supposed to be a Registry Cleaner. More on this later in the series. Finally we get the Installation button for KMPlayer. Bearing in mind, for the previous 4 steps, we have already agreed to and installed 8 assorted programs! Again more on this later in the series. Remember the PC Pro Cleaner which we ‘Agreed to install’ only a couple of minutes ago? Well it suddenly popped up, and found 4 errors in a couple of seconds, which is said required removal. Ummmm.. We continue to let it scan in the background. So now we have agreed, downloaded and installed our previous 8 assorted ‘wanted’ programs, plus the one we DID want, and NOW SEARCH PROTECT comes up, saying it requires installation. Note: it clearly states that Search Protect WILL set your home page AND your default search to TROVI Search for Internet Explorer, Firefox and Chrome. Not only that, it will ALSO prevent third parties from changing ‘my’ Browsers Home Page AND Search Settings. Ermm.. Hang on. Wasn’t this covered previously in the download.com policy settings?. But that’s right.. Because we have ‘ALLOWED’ the browser changes, and ALLOWED the programs to be installed, the policy settings from Download.com, mean squat. Now getting back to the PC Pro Cleaner, which was so conveniently installed for me. This had ‘found’ 41 errors. Nice of it to tell me. Again note, this is a brand new installation of Windows. There are NO errors! So we click on Activate We can get an instant $20 off, if we pay for the program now. So it would only cost me $29.95. Thanks, but I think I will pass. I know that this machine is clear of any and all issues.
See how easy it is for the likes of these programs to remove money from your wallet into their bank?. So until the next installment, PLEASE BE CAREFUL ON WHAT YOU CLICK, AND AGREE TO INSTALL! Next time, we will deal with YTD Video Downloader.
0 Comments
Welcome to PC Tech for Hire, Montgomery Alabama's dependable residential and small business computer repair and service provider.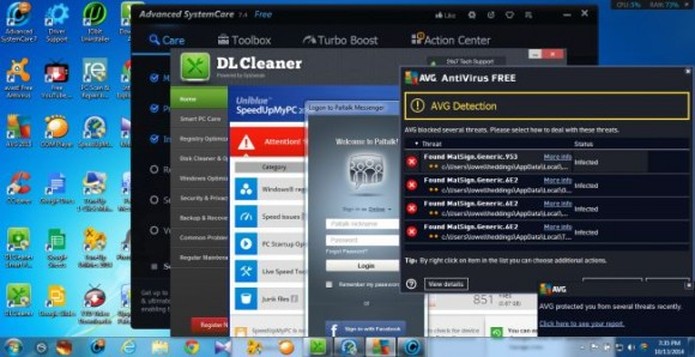 Thanks to Cadishead Computers for the use of this series of articles. Over the next few weeks, we will be writing a series of articles about the top 20 applications which can be downloaded from Download.com. Together with how these said applications install other assorted software behind the scenes.. This would read better as “what’s more YOU, yes You, 9 times out of 10 will allow this to happen!” When you do this, you’re allowing your computer to install assorted malware/spyware/viruses. So read on for what happened to our virtual machine, when we simply allowed each application to install what ever it wanted to. Together with the results of our malware scans afterwards. So, grab yourselves a cup of tea, or coffee, as you may not believe what happens... We installed the top 20 apps from Download.com, and you may not believe what happened to our virtual machine! Well… You may have a good guess, if you have already done something like install a free piece of software. Bad, bad things are what happens. It’s going to be a good series..Join us for the fun! For the purpose of this experiment, we have just clicked through all the regular installation screens with default options. i.e. we have NOT watched what we are downloading. This was done on a new install of Windows 7 on our virtual machine. We have installed the top 20 applications. You could be asking, why choose Download.com?. The reason is because their policies page clearly state that they DO NOT allow any nasty/bad/ virus infected software on their site. What’s more is that they do NOT accept any software which should have any of the following included inside it. Download.com does not allow malicious software on the site. We test all submitted software products according to comprehensive criteria. Viruses, spyware, and malicious software. We do not list software that contains viruses, Trojan horses, malicious adware, spyware, or other potentially harmful components. We do not list products known to contain such items in instances outside Download.com, and we may disallow products from publishers that we feel violate the spirit of this policy. We do not accept the following types of software: Software that installs viruses, Trojan horses, malicious adware, spyware, or other malicious software at any point during or after installation. Software that installs the above items via links to other software or Web sites.Links on publishers’ Web sites that may enable the installation of the above items. Software that installs without notice and without the user’s consent. Software that includes or uses surreptitious data collection. Software that collects and transmits information about end users or end users’ computer usage without adequate prior notification. Software that diverts or modifies end users’ default browsers, search-engine home pages, providers, security, or privacy-protection settings without the users’ permission. Software that interferes with users’ control and privacy. Well, with all of the above supposed protection in place from the very website itself, one that is supposed to be trustworthy, why should you worry? However, please note where it states ‘without the user’s consent’. What this actually means is, IF YOU DO NOT CLICK NO OR DENY, then it WILL install the other assorted software. So BE WARNED!. SERIOUSLY DANGEROUS!. DO NOT TRY THIS AT HOME! If you do attempt this at home, then DO NOT be surprised when your computer wants you to put it back into the box it came from, and return it from whence you bought it. Either that, or take it to a professional to clean up everything that you have done.. In fact, if you have already installed any of the software we are going to mention here, it would be a good idea to have your machine looked at by a professional!. We have mentioned previously against why you should not use supposed ‘System Tune Up’, or ‘Registry Cleaner’ programs. So where do we start off. We fired up our virtual machine, and went directly over to download.com. The first thing we did was to go to the windows downloads page, and see what we could download from the 20 most popular downloads. This list may change at a moment’s notice, but this is as it stands today.  The list of the current top 20 programs are Avast Anti virus – Protect your PC and data from hackers and thieves. KM Player – Play digital media of various formats including incomplete, partially downloaded, or locked files. AVG Anti virus 2015 – Protect your computer from viruses and malicious programs. YAC – Protect your PC from browser hijacker, malicious plug-ins, malwares, adware, various viruses. CCleaner – Clean up junk files and invalid Registry entries. Advanced System Care – Speed up a slow PC, shorten startup time, and protect online privacy. Free You Tube Downloader – Download YouTube videos and convert to multiple formats. YTD Downloader (You Tube Downloader) – Download and convert videos from video streaming sites. IObit Uninstaller -Remove unwanted apps, browser plug-ins/toolbars and Windows 8 pre-installed apps thoroughly. Download App – Keep the software on your Windows computer up-to-date and running smooth. 3DP Chip – Download the latest device drivers with few clicks GOM Media Player – Play video files of multiple video formats. Virtual DJ8 – Mix digital music or video replacing your turntables and CD players. Malwarebytes Anti Malware – Detect and quickly remove malicious threats to your computer. Photoscape – View, edit, print, or add frames to your photos. Start Menu 8 – Bring back “Start” menu for Windows 8/8.1 and advanced start menu for Windows XP/Vista/7 and 10. Driver Booster 2 – Update drivers from online database in one simple click. Internet Download Manager – Increase your connection speed and recover broken downloads. VLC Player – Play audio and video files in real-time and streaming modes. Ad-Aware Anti virus – Protect your personal computer against virus and spyware attacks. This list is good to know what NOT to download. The plan is to download and install the top 20 programs. Although as you can see in the list above, within the top 3 programs, 2 are anti virus programs and the last one is Ad-Aware Anti virus. Since we only want one, and we detest AVG with a passion, and have never used Ad-aware AV, we are just going to install Avast. Surely one of the top rated (in terms of downloads) will stop our machine from being infected with a virus etc? Therefore for the testing purposes of this series, we will only be downloading and installing 17 of the above programs. Results may differ from our testing to yours in a real life scenario. Please bear in mind this is a fresh windows install. With nothing else installed at the time. No windows updates, no programs what so ever! 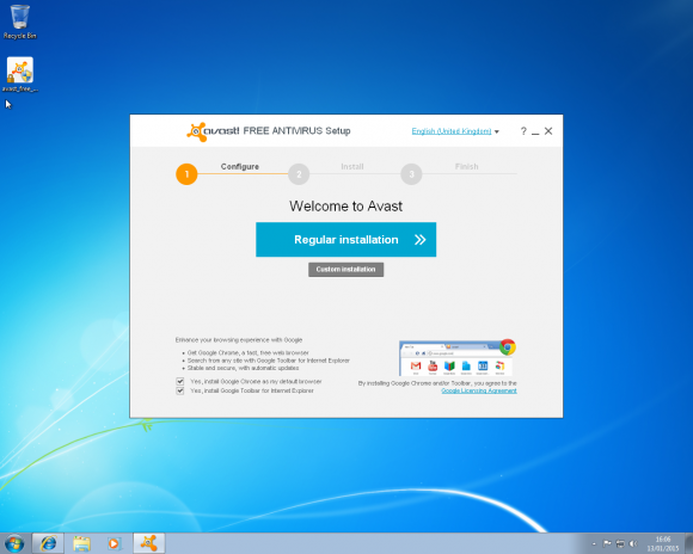 Avast Anti Virus. Bundled software is the same as in-app purchases made on a mobile phone. Here to stay, unless you say no! Well this time, it is not spyware/bloatware/malware being installed, as well as Avast. Google Chrome is a fantastic browser, and one of our favoured ones. However the bundling of software starts right here. The free software vendors make more money by allowing bundled software to be installed with their installations than they do by selling their own software. This is our own personal view. This time, at least, Avast is bundling something good, but it still breaks Download.com’s policies wouldn't you say? Our next installment will be KM Player. Thanks again to Cadishead Computers for the use of this series of articles. I hope you'll benefit from the information that will be given throughout the series. This will definitely be a learning experience! Hopefully you'll learn what NOT to do when downloading and installing programs. But, if you get in a bind, I'm always here to help! Click on my Contact Page to send me a message and I'll get with you as soon as possible. Welcome to PC Tech for Hire, Montgomery Alabama's affordable residential and small business computer repair and service provider. The world of computing can be a confusing place. PC Tech for Hire has put together a simple jargon buster to help you understand some basic aspects of the world of computing.
Anti-virus: Anti-virus software provides you with extra security from computer viruses. Broadband: Broadband is a method of connecting to the internet. Broadband enables large amounts of data to be transferred at faster speeds than dial-up. Browser: A browser is a computer program that enables you to read and view websites over the Internet. Computer Programs: Computer programs contain a set of instructions for your computer to follow. A computer program does not run its instructions unless executed by the CPU. CPU: The CPU or processor, is the brains behind your computer. The CPU is responsible for executing your computer programs. Dial-up: Dial-up is a way to connect to the Internet using a telephone line and a modem. Email: Email is the exchange of electronic mail between users around the world. Firewall: Firewalls provide extra security which protects your computer from unauthorised access by crackers. Graphics Card: A Graphics Card, also known as a video card, is a component which generates and outputs images to a display. Hacker: Hackers are people who enjoy exploring and learning about computer systems. They are often confused with crackers, who often break into computer systems to steal information and cause as much trouble as possible. Hard Drive: The Hard Drive stores your data on your computer. Unlike RAM memory, when power is lost, the data remains intact. Hyperlink: A piece of text or image, that when clicked takes you another web page. Internet: The Internet is a network of networks around the world. The Internet is responsible for data communication. IP address: An IP address is a unique numerical number assigned to devices connected to a network. Memory: The main type of memory inside your computer is RAM. Ram (random access memory) stores data temporarily in your computer. When the computer is switched off, the data is lost/erased from the RAM. Modem: A modem is a device that allows computers to send and receive data over telephone lines. Motherboard: The motherboard is a circuit board, which provides a way for your devices to communicate with each other. Network: A Network is when two or more computers are connected together to share resources and information. Router: A router is a device that allows two or more networks to be connected together so data can be transferred between them. Server: Is a powerful computer system on a network that stores data and also responsible for resource management. Sound Card: A Sound Card is a component which generates and outputs audio/sound to a set of speakers Switch: A device that networks two or more computers together. URL: URL (Uniform Resource Locator) is a way to locate a file/website over the Internet. For instance, the URL for SJH Computing is http://www.sjhcomputing.co.uk USB: USB (Universal Serial Bus) is a way to connect different devices, such as digital cameras to your computer. Virus: A computer virus is a program that is designed to cause damage to your computer. Web page: Is a document hosted on the Internet, which when combined with other web pages creates a web site. World Wide Web: The World Wide Web is a collection of interlinked hypertext documents which is accessed via the Internet. Have any questions you would like answered on my blog? Contact me here with your question, and you will see a response in a future blog post. Welcome to PC Tech for Hire, Montgomery Alabama's trusted residential and small business computer repair and service provider. When it comes to anti virus & spyware programs, just how much difference is there between the paid for versions and the free ones?
In the “olden days” when computer viruses were just beginning to hit their heyday, you had to pay for all virus protection software. Nowadays, there are plenty of free virus protection programs available for users to download from the Internet. There are also many paid programs available, so you may be wondering whether you need to pay for virus protection software or if the free programs are adequate. To answer that question, you need to determine what your virus protection needs are and in what capacity you will be using your virus protection program. For example, the majority of free programs are designed for personal home use only, not for business use. So if you’re looking for virus software for your business, you’ll have to purchase a licensed version. There are several other differences between the paid and free versions as well. Performance The main reason you install virus protection software is to protect your computer against viruses, which can harm your computer. Tests have shown that both the free and the paid virus protection programs perform comparably in terms of detecting viruses on a computer. While this is incredibly important, there are other types of malicious programs and components that can infect your computer and cause irreparable damage or steal personal information. Detection and removal of spyware, malware and other nasty items is where the paid programs shine. Most of the free programs also detect malware, but the paid programs do a better job and detect more of the little nuisances, which means your computer is cleaner and your information is safer if you’re using a paid program. Additional Features Another way paid virus protection wins over users is by offering additional features. When comparing virus protection programs, you should take a look at these added features and see if any of them appeal to you. Examples of added features include parental controls, enhanced spam filters and identity theft protection. Avast’s paid program, Internet Security 6 Package, even opens up a new desktop for sensitive information, such as online banking, so other programs cannot steal account numbers or passwords. Support One of the major differences between free and paid virus programs is the customer support. Support is typically lacking or nonexistent with free programs because there is no money being exchanged. You may find a FAQ section on the company’s Web site or a limited help section built into the program, but the companies offering free software typically do not invest much money in support for these free programs. Paid programs, on the other hand, typically offer online and phone support for users. While you may not consider support to be a big deal, keep in mind that the free programs are often a bit more difficult to operate and navigate. If you decide on a free program, but are unable to set it up properly, it is useless. If you’re still unsure of whether to go with free or paid virus protection, think about how you use the Internet. For users who are frequently downloading files and surfing a wide range of sites, a higher level of protection is warranted. For people who do minimal surfing, do not download many files and do not use credit cards online or engage in online banking, a free version is most likely fine. You could always see if the paid program you like has a free trial and compare it to a free program for yourself. That way you’ll know if it’s worth spending the money each year for the paid version. Good luck, and stay clean from those malicious viruses! For a quality paid service, look no further than my ProActive Care - Antivirus service. Not only do you get the benefits listed above for a paid service, you get the added bonus of having someone actually monitor the service. I will keep an eye on virus scans to make sure viruses or other malware is being detected and removed correctly. And in most cases, my service costs less than other paid solutions. Contact me for a free trial! |
Ronnie MorganHi! I'm Ronnie, your PC Tech for Hire for the Montgomery, AL area! Let me know if you need my 25+ years of experience to help you with your computer needs. Archives
January 2018
Categories
All
|

 RSS Feed
RSS Feed