What is "Ransomware"?Welcome to PC Tech for Hire, Montgomery Alabama's dedicated residential and small business computer repair and service provider.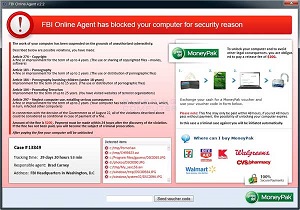 Ransomware is a type of computer virus that "holds" your computer hostage. These type of viruses can prevent you from using the internet, your computer, specific programs, or in some cases, encrypt your data. One thing these viruses all have in common is that they want you to pay them in order to release your computer from their grasp. While some keep their word, and once you pay they delete themselves, not all of them do and they simply take your money and ask for more. Common payment methods include Moneypak, Paypal, wire transfers, etc. I'm only going to outline the more common of these, what they look like, and what they are going to do. 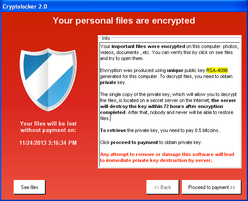 The FBI virus is the more common one for those in the United States. There are many versions of this one, some claiming to be Interpol or another local police agency to your country or region. One thing that really makes this trojan virus stand out is that it pops up your screen on says your computer has been used for illegal activities such as pirated software or child pornography, and your actions on the computer are being monitored by law enforcement. The warning informs you that in order for you to have your computer unlocked, and the charges dropped, you must pay a fine using an anonymous prepaid cash service. This virus will give the illusion that this is real, but this is not how law enforcement works. If they knew where you were, and what you did, they'd knock on your door, not lock your computer. While many antivirus programs do in fact prevent or even remove this virus, this virus is not always traveling alone. One of the things this virus does is send a few of its friends in first. These friends will disable your computers security, or stall it, so the virus can get in there and take control of the computer. So how do you get this virus? Typically it is done through downloading what appears to be legitimate software from websites, especially torrent downloads. The less common way is through drive-by means, or visiting a website that has been infected to download the virus without your knowledge in the background. In some cases, this virus can be removed remotely, but in most cases the computer has to be cleaned of this virus either on site or in a shop. It is strongly encouraged to have the FBI virus removed by a professional as this virus can return after a computer has been restarted if it has not been removed completely or correctly. To really prevent yourself from getting infected, make sure you only download software from a legitimate website, and never download unverified torrents or pirated software. CryptoLocker came out in mid to late 2013. This is a computer worm virus, or one that spreads through your network. The mission of this virus is to encrypt your files and hold them for ransom. Typical infections are via attachments in malicious emails, and most recently through drive-by downloads. Once the CryptoLocker downloads on to your computer, it generates a 2048-bit RSA encryption key, and uploads it to it's server. Once the key has been generated, it begins encrypting data on any local or network storage device that your computer can access, targeting files matching a specific whitelist of file extensions. The virus will inform you of its presence, and include a count-down (typically 3 to 4 days). Once the countdown has hit 0, everything the virus was able to encrypt has been encrypted, and the encryption key deleted, making recovery impossible. CryptoLocker will demand a payment, we've seen as low as $200 and as high as $600, in order for your files to be encrypted, but the decryption process must start before the countdown hits 0. Any files that have been encrypted can not just be decrypted, a 2048-bit encryption key would take thousands of years to discover. But do not fear, there are many things that can be done to safeguard your computer, and recover lost files. Protection Make sure you perform regular backups of your computer. Whether it is ProActive Care - Backup or any other means. If you use an external hard drive, remember to unplug it and store it somewhere safe to keep this drive being encrypted as well. Install CryptoPrevent or call us to install it for you. Once Infected The number one thing you should do once you discover your computer is infected is turn it off. The virus can not encrypt files if the computer has been turned off. Some claim that unplugging it from the internet will stop it from encrypting, this is not true. Next, do not pay the ransom. The biggest reason is because you would be feeding a criminal and recovery can be less than what the cybercriminals are asking for. Give us a call immediately to have your computer recovered from this virus. We will have to take your computer, and turn around times for recovery do vary. Make sure to give us all the backups you have, or access to your online storage backup. Other Ransomware Viruses Windows Product Activiation is another worm virus that is not as famous as the other two, but it gets the job done as far as what it does. If you've already activiated your Windows installation, you should not have to do this again unless you replaced a major hardware component inside the computer itself. Always consult us before you write this off as a virus. This virus informs the user that you have to re-activate your copy of Windows due to being a victim of fraud. There will be a pop-up trying to take you to a website (a link that normally does not work), and instead has you call one of various international phone numbers to input a 6-digit code. While the claim is that the call would be 100% free, the call is actually routed through a country with an extremely high international phone rate, and then they place you on hold for a long while. This causes the user to incur a very large long distance charge. If you believe your computer to be infected with ransomware, or any other type of malware, please contact us for a Virus Removal service. Ask about my ProActive Care - Antivirus service that can help prevent a lot of these types of ransomware and malware.
0 Comments
Laptop Buying GuideWelcome to PC Tech for Hire, Montgomery Alabama's premier residential and small business computer repair and service provider. This is the time of the year when people are looking for that perfect gift. And what could be more perfect than a new laptop!? I'm often asked what laptop they should buy, which one is the best, etc. All models of computers/laptops will end up having a problem at some point. My opinion? Follow these simple rules and you just bought the best laptop! 1. Figure out a budget. Remember that with a new computer, you may need to buy new software. And for those that want help setting it up, I quote 2-3 hours to get everything installed and configured. 2. Make sure you buy a laptop in person. Buying online gives you no sense of how the computer feels, weighs or views in bad/good/extra light. If you buy online, be sure to buy from a reputable company that you know you can return items too easily. 3. If you go to a store, here are some tips!
A good work laptop is approximately $500-$900. You will pay more for higher quality (SONY) and of course for a faster processor, solid state hard drive and more options (longer battery life, docking station, etc.) Many folks also ask about the processors and hard drive space, etc…my answer is you’ll be ok probably if you can find a computer that fits your needs with the list above. Those are much more important. Most computers today come with plenty of hard drive space. Don't forget to include my ProActive Care services with the purchase! Help your new purchase last longer with ProActive Care - Antivirus, and keep backups of all your data withProActive Care - Backup!  Welcome to PC Tech for Hire, Montgomery Alabama's professional residential and small business computer repair and service provider. In the famous words of Joni Mitchell, you don't know what you've got until it's gone. Unfortunately for many home computer customers, not having a reliable data backup solution is a painful lesson to learn. As we all become increasingly dependent on our digital files, having a copy, or multiple copies, of those files is a crucial element of keeping your data safe. The data on your computer or mobile device can disappear in an instant - succumbing to accidental deletion, corruption, malware encryption or theft. The best way to prepare for a data disaster event is to make sure that you have a workable, reliable and verifiable backup solution in place. A Workable Backup Solution The first thing that you need to do when considering backing up your data is to find a solution which works for you. People use their computing devices differently, and therefore a backup solution should work with your computing experience. Are you the type of person who prefers to control exactly when you backup your data or would you rather "set it and forget it"? Do you prefer having your data close by, say on an external hard drive, or would you rather have it available 24x7 via the Internet? Does your data reside on just one computer or on multiple devices? Answers to these questions will help you decide on the best backup solution for your situation.  4 Key Elements that Every Backup Scheme Should Have Your backup needs to be automatic. Life is too busy for most of us to consistently remember to start backing up our data. Most backup software and services, though, can be scheduled to start automatically. Some programs even backup instantly every time a file is added or changed. Don't let it be your job to remember to plug in a storage device or to kick off a backup routine. Let your chosen solution take care of that work for you. Your backup should be verifiable. Many people have a backup plan in place, but unfortunately not many have a restore plan in place. If you are not sure whether or not you can successfully recover the files that you have supposedly backed up, then you don't have a backup plan! Part of your backup routine needs to be periodic testing to make sure your backups are valid. This may be doing something as simple as restoring one of your files or folders to an alternate location on your computer. If you can regularly successfully restore files from your backup when you don't necessarily need them, then chances are better that you will be able to restore them when you do need them. Your backup should Include versioning. It may not be enough to have just one copy of each of your files. As many who have been hit by the Cryptolocker infection have discovered, backup solutions which don't keep multiple copies of files as they are changed are susceptible to being overwritten by malware. Therefore, it is important that your backup solution allows you to restore copies of your files from various points in time in the past. Your backup should be secure. Do you keep thousands of dollars under your mattress because you feel it's more secure than keeping your money in a bank? Many people follow a similar strategy when it comes to protecting their data. Don't assume that your data is secure just because you have a copy of it on an external hard drive attached to your computer. Hard drives can fail at any moment, can be stolen or can fall victim to a virus or a power surge. However, cloud-based backup solutions are, for the most part, much more secure than onsite backups. Most offsite backup solution providers keep their customers' data in tier 1 data facilities with multiple levels of security controls, encryption, environmental protection and co-location. It is safe to say that your data is better protected in one of these "data banks" than under the proverbial mattress in your home.  Backup Solutions that We Recommend PC Tech for Hire has two different backup solutions that we recommend. We offer two solutions because each of them is able to cater to the different backup needs of our customers. The first solution that we offer is Backblaze. This backup company has been in the business longer than most of the others, and it has a reputation for simple, affordable backup services for residential customers. Backblaze's user interface is very easy to understand, and customers are able to determine whether or not their data is secure just by looking at the file names on their computers. Backblaze offers unlimited backup for your home computer for just $50.00 per year, or for $5.00 per month. The second backup solution that we offer is a solution which offers local backup, versioning and fully encrypted backups locally and in the cloud. While the cost per gigabyte is more than Backblaze, my ProActive Care - Backup service allows you to protect multiple computers under the same plan. Therefore, if you are a household with 1-5 computers, this backup solution would probably work better for you and would be cheaper in the long run than Backblaze. Furthermore, ProActive Care - Backup is monitored regularly. That is, we will take on the responsibility of making sure that your devices are being backed up and that your data is able to be restored when needed. The cost for ProActive Care - Backup is $9.00 a month for 10gb of data, and $99.00 for an annual subscription. Larger blocks of data are available if 10gb is not enough. Contact PC Tech for Hire for a custom quote. Both of these backup solutions provide automatic, scheduled backups to a secured data center, easy restoration procedures, versioning and 24x7 access to your files from anywhere via the internet. Making sure that your data is backed up securely is not a difficult task in today's world. However, it does take a bit of planning and initiative on the front end. However, when a data disaster strikes, you will be glad and grateful that you have a solution in place. Welcome to PC Tech for Hire, Montgomery Alabama's dependable residential and small business computer repair and service provider. Be aware of online scams! Tis the season, they say, but what they don’t say is it’s also the season to be scammed. Holiday shopping time is the perfect time for unscrupulous people to exploit peoples holiday cheer to gain access to accounts, steal identities and do other things that should earn them a lump of coal in their stocking. So what do you do to protect yourself? What types of scams should you be on the lookout for? “Your Order Has Shipped/Problem With Your Order/Confirm Your Order” This one’s a popular one because it takes advantage of people not wanting to “mess up” a holiday gift. This e-mail may look like it comes from a popular merchant (Amazon, Walmart, etc) or may be one you've never heard of, and will ask you to confirm or view an order. Once you click the link you are brought to a website which may look legitimate, but is actually designed to steal your login information or collect credit card information. How do you protect yourself? Simple: If you think it’s legitimate, log in to the website by typing the merchants website in to the browser manually – not clicking on the link. If there is an order there, you’ll see it where you normally see your orders (usually under My Account or Orders).  “A Gift Is Waiting For You/Free Holiday Offer” This one exploits the warm feeling you get when you receive a gift, and as we all know, everyone enjoys getting gifts. If a person sends you an e Gift or virtual gift card you may get an e-mail with a link to claim it. You may also get an e-mail claiming to be a free holiday gift for being a valued customer or long time member of an organization. How do you protect yourself? This one is a bit harder to protect yourself from, but it’s a good idea to mention the gift to the person who allegedly sent it. If the gift was from a friend, call or text them and say “I just got an e-mail with an iTunes gift card from you, is this really from you?.” You can also hover your mouse over the link and verify the address goes to the merchant’s known domain name (Apple gift cards should go to Apple.com, Amazon to amazon.com, if one goes to amazon.somenamehere.com, then that’s not really Amazon.) For merchant gifts, call or e-mail the merchant to verify that the offer is real.  “This Price Is Too Good To Be True/90% Off Sale Going On Now” This scam exploits our greed and most people’s enjoyment of getting an amazing deal on something. You will see an offer for a 47" LED TV that usually sells for $800 for $200, or a high end digital SLR camera that normally sells for $500 for$150. You may also see e-mails claiming an amazingly high discount off listed prices on a website that’s given back by mail later or returned to you 30 days after purchase. How do you protect yourself? If a deal is “too good to be true”, it probably isn’t true. If a merchant has a limited loss leader for a retail store or a website (where they sell an item at cost), then that’s possibly true, but expect a very limited number and needing to be the first few online to get one. If an item is sold so far below every other vendor – even below the reasonable cost to make the item – something is probably up. The best way to protect yourself here is to be suspicious and only go for “amazing deals” from trusted vendors you know and have already done business with. A good bit of common sense and reasonable suspicion will protect you when shopping this holiday season, but don’t let these few bad apples spoil your fun. Another way to protect yourself is with my ProActive Care - Antivirus service. My Antivirus/Antimalware service monitors your Internet browsing activity and warns you when you are about to enter a site that is either questionable or is a known malware site. The suggestions I give above should always be followed, however, my ProActive Care service will give you that extra layer of protection. You may be going to malware sites and not even realizing it. Contact me today for a free trial!
|
Ronnie MorganHi! I'm Ronnie, your PC Tech for Hire for the Montgomery, AL area! Let me know if you need my 25+ years of experience to help you with your computer needs. Archives
January 2018
Categories
All
|

 RSS Feed
RSS Feed